VNC is kinda really very insecure. At least, the “official legacy” implementations were.
VNC stands for Virtual Network Computing, and is a form of remote desktop control software (like TeamViewer, Splashtop, Chrome Remote Desktop, etc…).
Under the hood, it relies on the RFB protocol (RFC 6143) to send mouse and keyboard inputs to, and receive the display from a computer.
Unfortunately, implementations of VNC lack in security, and it’s strongly recommend not to expose any VNC ports, especially over the internet. Unless you’re using a more secure implementation of VNC - like what RealVNC offers - even exposing your VNC server to your local network is discouraged - you never know if there’s a malicious device on your network!
If you take a look at where your VNC password is stored ([HKLM]/Software/[...]/WinVNC... for Windows systems, ~/.vnc/passwd for Linux), you can see that the password is encrypted… though it’s rather short at 8 bytes in length..
My VNC password is encrypted, phew!
So anyway, there’s a bunch of tools that can read / decrypt / extract the VNC password: patator, vncpwd, VNCPassView, Cain and Abel, this old site
In fact, if you have openssl installed, you don’t need need to download any of those tools! (source)
Assume the string from the .vnc file is
d7a514d8c556aade
echo -n d7a514d8c556aade | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d -provider legacy -provider default | hexdump -Cv(btw I think the
e84...ae0string
The output will look like the below
00000000 53 65 63 75 72 65 21 00 |Secure!.|
According to RFC 6143 (Section 7.2.2)…
The client encrypts the challenge with DES, using a password supplied
by the user as the key. To form the key, the password is truncated
to eight characters, or padded with null bytes on the right.
We can see this behaviour in TurboVNC’s / TightVNC’s vncauth.c file.
Also, amusingly…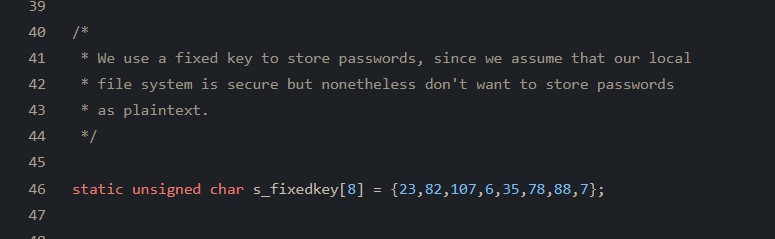
In effect, your 8-character (max) password is used as the DES key in the encryption challenge.
If you have a longer-than-8-character password, only the first 8 characters are used.
If you have a shorter-than-8-character password, the key is padded with zeros.
In other words, your password can only be at most 8 characters long…
Whilst it’s not as bad as Westpac’s password length requirements, 8 characters seems pretty short considering the rate of authentication attempts that you can perform.
But I don’t have access to the VNC password file!
Eh, if you can view the network traffic, supposedly you can crack the challenge-response pairs with a tool like VNCcrack.
https://www.randombit.net/code/vnccrack/
VNCcrack is a simple, fast offline-mode VNC password cracker.
It takes a set of challenge-response pairs of the type passed during a VNC authentication attempt,
and attempts to recover the passwords using a dictionary file.
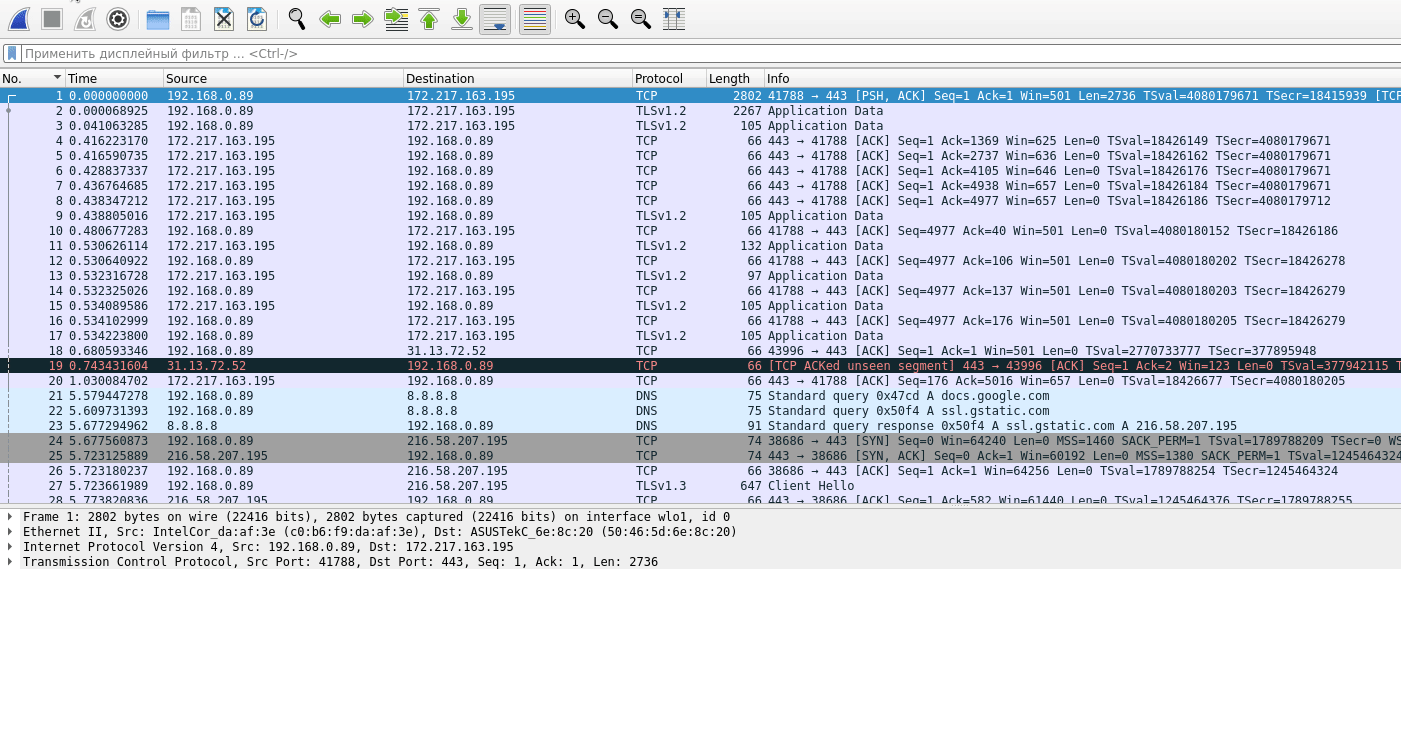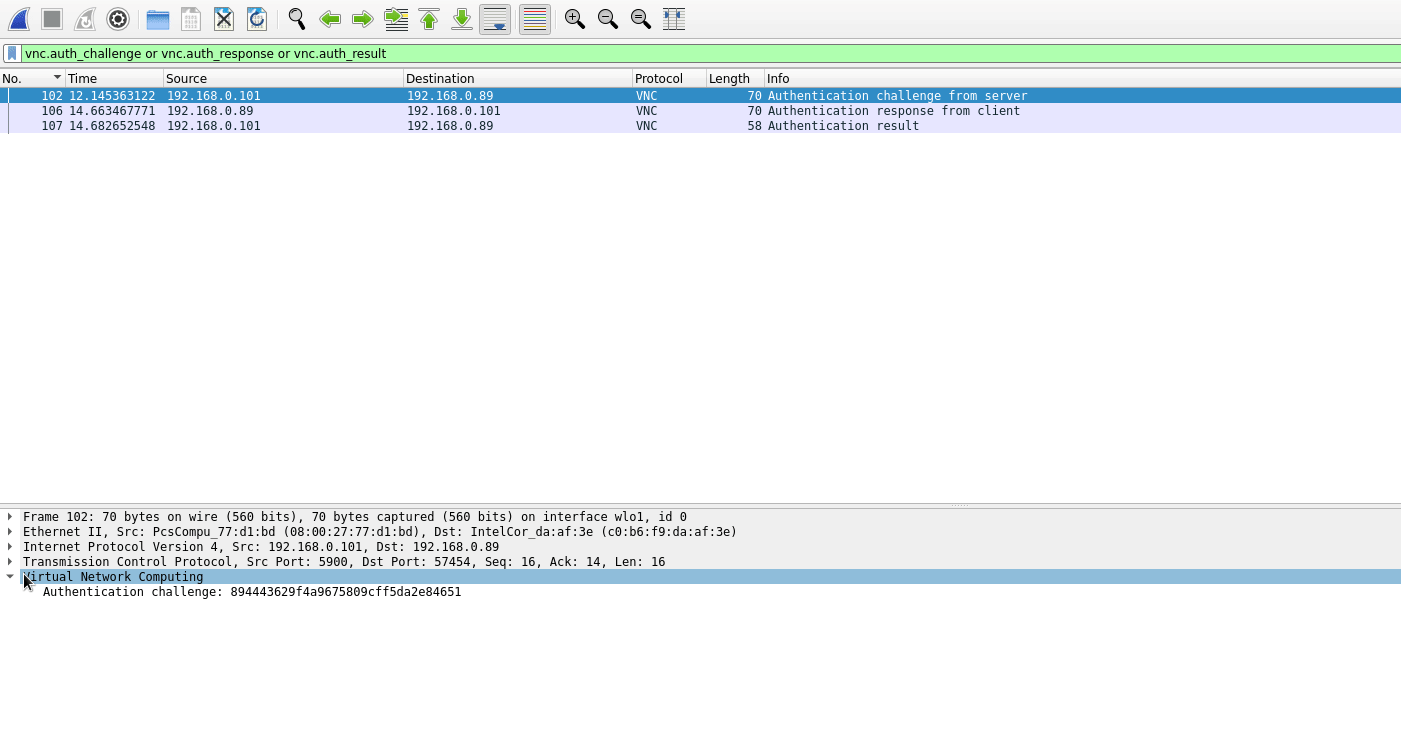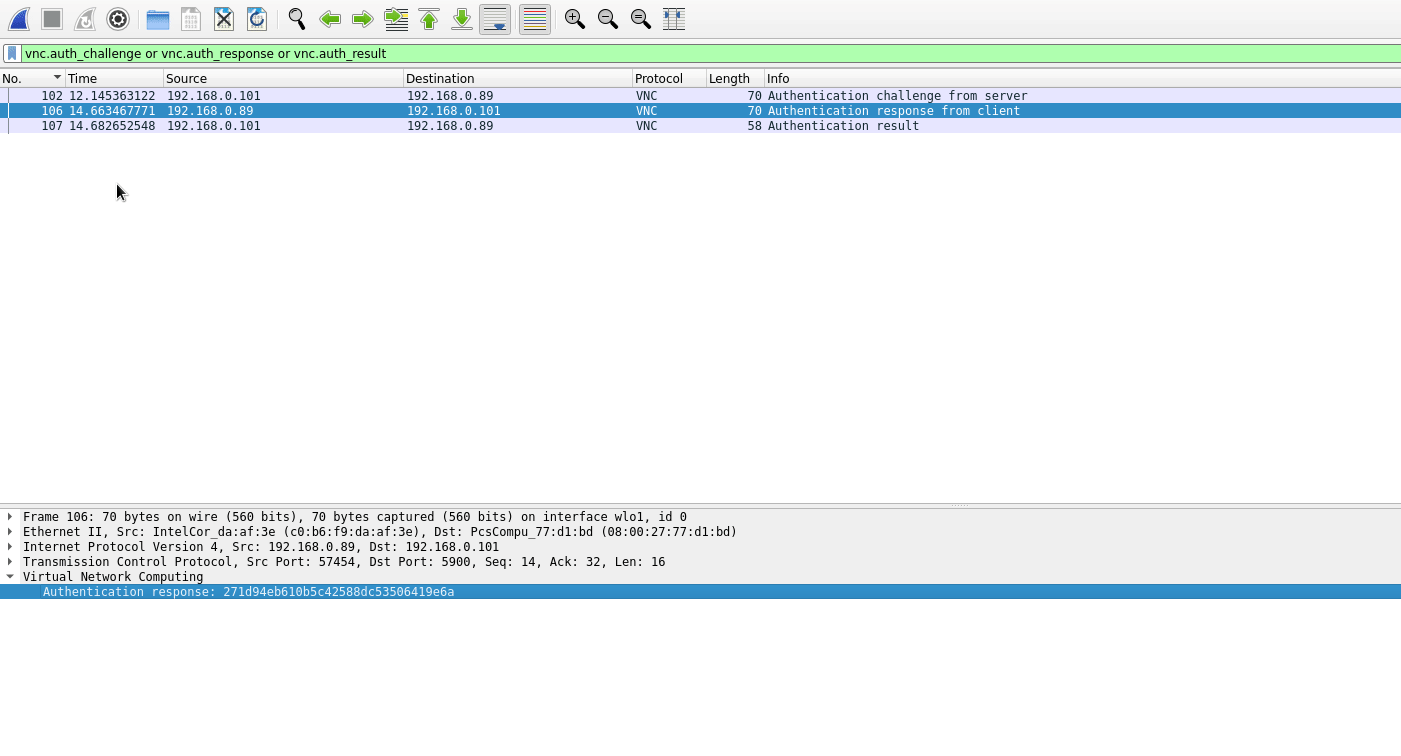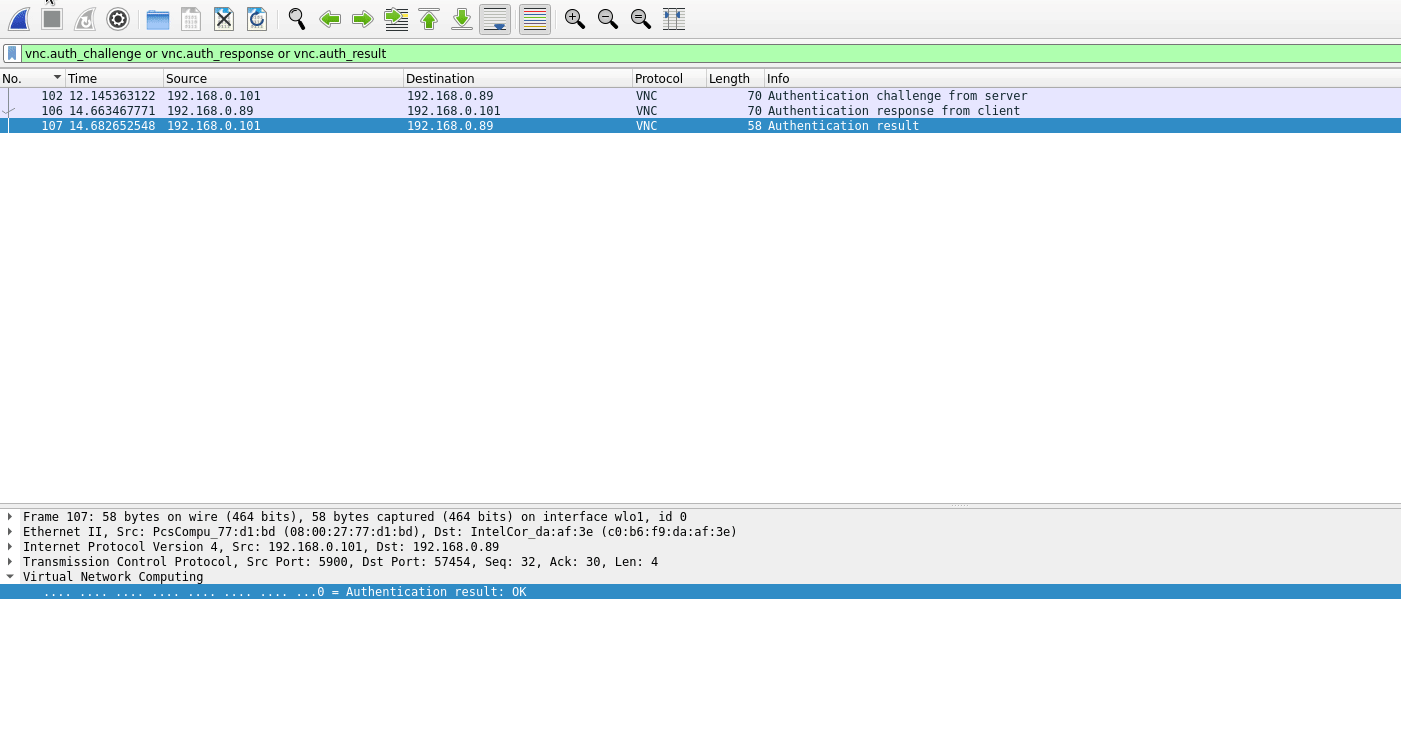
Source: https://miloserdov.org/?p=4854
There’s also a bunch of other information that you can extract, like the VNC server’s computer name, mouse button positions, and just everything you probably don’t want others to see
Thankfully no one listens to standards!

Source: https://xkcd.com/927
With companies like RealVNC, “VNC” is literally in their name - and they haven’t gone under… so they’re doing something right!
Thankfully, as mentioned in RFC 6143 (Section 6) you’re free to use your own frame encoding implementation and importantly, your own security implementation.
This lets you mitigate the previous problems, and instead rely on more robust authentication schemes - like RADIUS, AD, … or just something more secure than a hardcoded encryption key™
A list of implementation extensions can be found in RFC 6143 (Section 8.1.2), but supposedly this document is more up to date.
TL;DR Don’t use VNC
But if you do, don’t use the legacy authentication methods…
Use a real VNC tool, like RealVNC!
Not sponsored.