It’s that time of the year again where my uni society holds a CTF competition!
If you don’t know what a CTF is…It’s a competition where you solve challenges (often computer / forensics / hacking related things) to get the highest score.
Last year my team won despite two people (of our team of 4) going AWOL. This year I paired up with my other half of a brain cell to form a team of two.
Whilst we weren’t eligible to win prizes (that are hands down better than last year’s) we still decided to do it anyway - It’s not for the prize, it’s for the experience (and personally, a reason to write yet another blog post here) 😉!
As per the usual flex-like attitude: Though we started the challenges on time (last year we started 2 hours late) we were a small team of two, competing against teams of threes or fours. But thanks to our unfair advantage of being keyboard warrior, and not being beginners in this “Newbie competition” we still came “first”!
Of course, it’s not a feat to announce coming first against beginners; but my saving grace is that we competed and came first over the other CTF veterans who were also competing for fun.
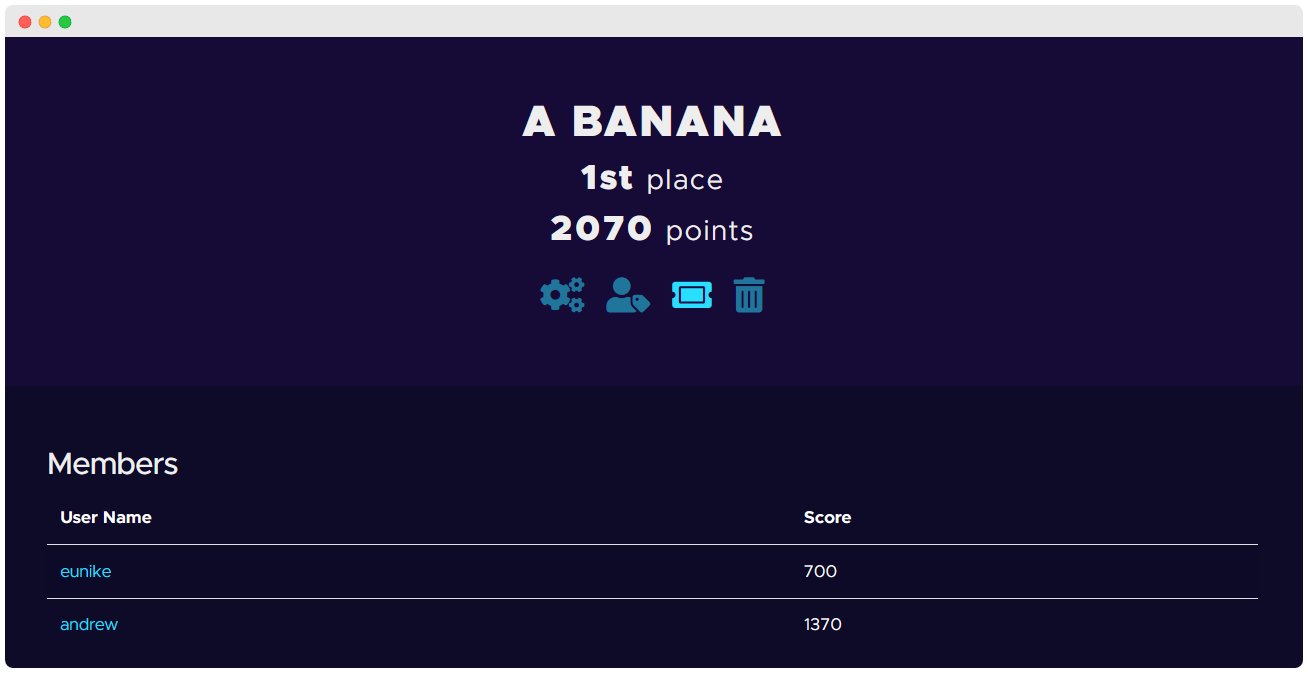
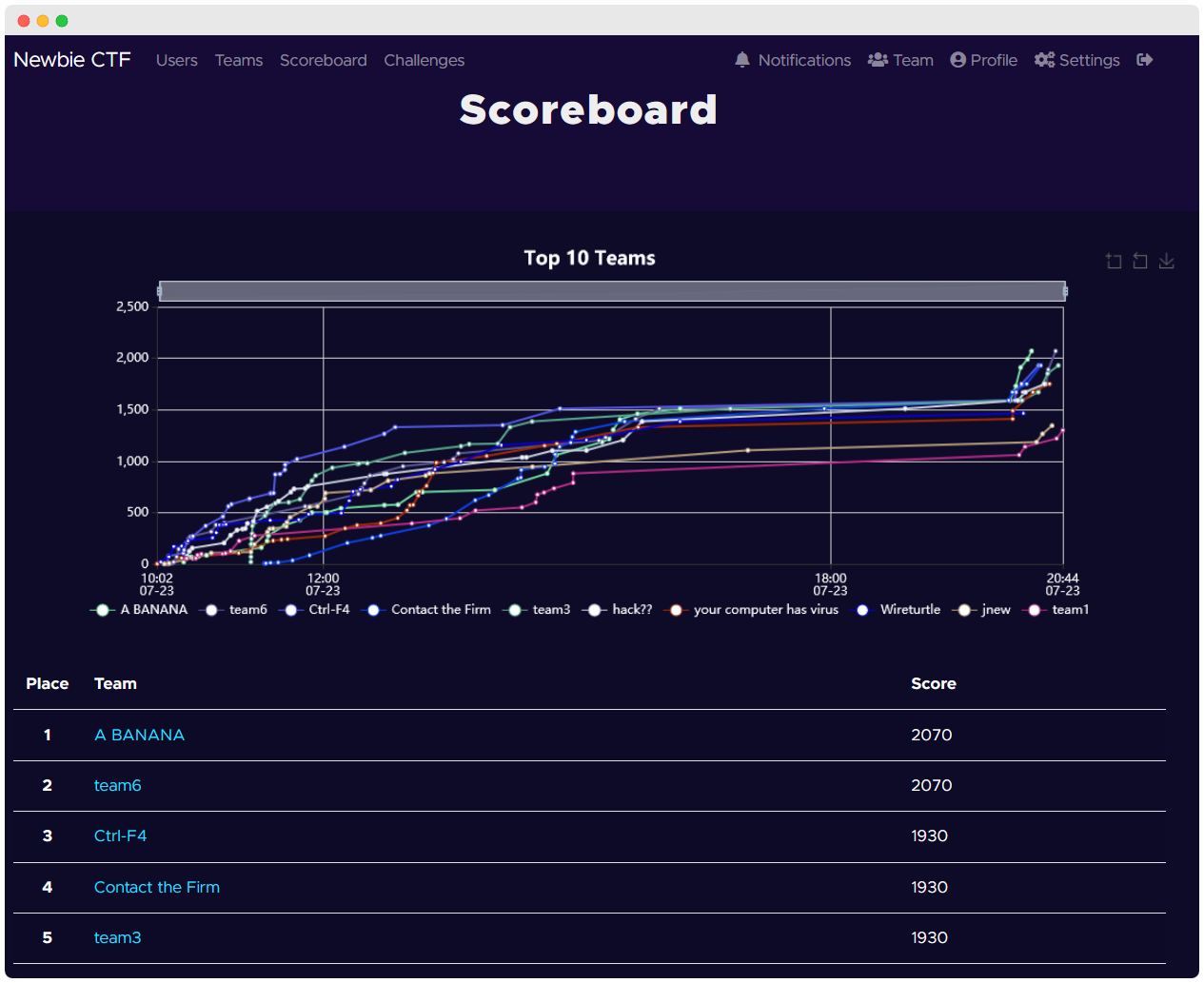
Here’s some fun stats when the second lot of challenges were released during the evening of the CTF competition (prior to this there were five or six teams who had the same score, the earlier teams to reach the score get a higher rank).
Our team (A BANANA) (well just me) spent around 20 minutes to pump out the new 6 challenges, and just like that we claimed the ineligible first place!
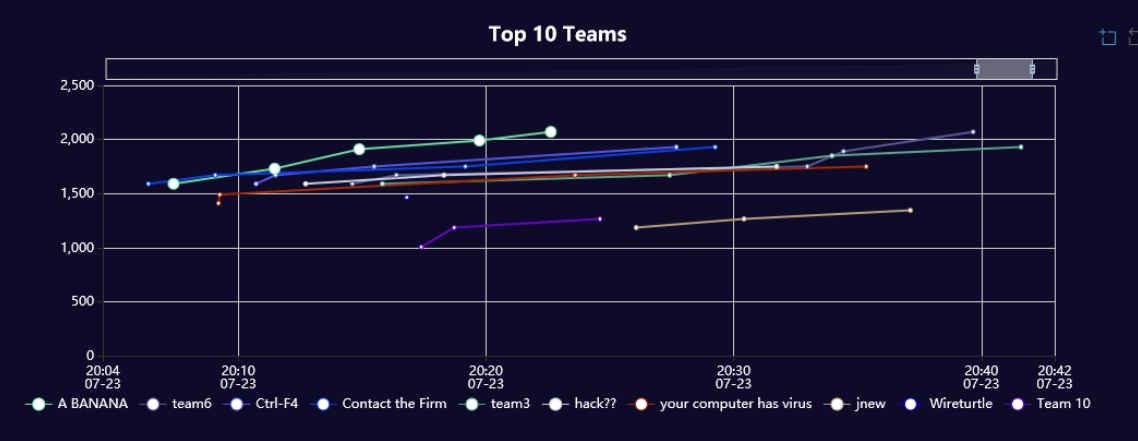
Anyway, so as usual, here’s the writeups for the challenges that I did
Category: Web
Oregano Cafe
Part 0
Flag found in the robots.txt file
robots.txt
# Part 0 Flag: NEWBIE{be3p_b00p_tH!s_siT3_was_pLaGiar!s3D_i_m34n_syNth3sized}
User-agent: *
Disallow: /starch.py
Flag: {be3p_b00p_tH!s_siT3_was_pLaGiar!s3D_i_m34n_syNth3sized}
Part 1
Upon trying a password, the website gives an error as well as the expected hash (a4ec243c744c8424fcb454f4cc4464246ca40484243cd454bcf41424fc048c04). From the robots.txt file, we can see a file starch.py, which when viewed shows the implemented hash function.
Reverse engineer this function to find the password which can be put in.
There is more than one correct password, due to how the hashing function handles the last character of the password input.
Password: lo2eme30m5f2e5h0o0440e3nom.pmn/5
Flag: NEWBIE{wriTinG_y0uR_0wn_ha5#_fuNcTi0N_iSnT_th3_b3St_id3A!}
Script: sol.py
SecBin
File uploader which has and endpoint that allows you to view the file… or any other path in the filesystem. So we can do some LFI (Local File Inclusion) and Directory Traversal exploits to leak some secure files… like /etc/passwd
URL: https://secbin.ctf.unswsecurity.com/download?file=../../../../../../../../../../etc/passwd
Flag: NEWBIE{1m491n3_54y1N9_1T5_uH4x0r4bL3}
Category: Binary
no_code_attached
Given ASLR/PIE protection and a lack of address leak, we know this is not a
ret2winchallenge.
The vulnerable function in the binary file reads in a password string and returns (as eax) the contents at ebp-0x10. The main function compares this result to 0x4269 and calls the win function (top_secret_admin_stuff) if it matches.
We can exploit the input loop to override the contents at ebp-0x10
Flag: NEWBIE{h4v1ng_th3_c0de_sur3_h3lp5}
Script: sol.py
Category: Forensics
whitespace
MS PAINT OP
The flag is handwritten in a slightly different colour than the background. Use a magic wand selection tool / change the background colour.
Flag: NEWBIE{it_flooded}
My Favourite HEXagon
View the image as hex to find the flag (or like, use strings), in a reversed format.
Flag: NEWBIE{h0w_d1d_u_f1nd_me}
world emoji day
A bunch of images, a text file and a corrupted ‘image’ is provided in a zip file. Looking at the corrupted “image”, it is actually a corrupted PDF file (given away by some metadata tags). Throw it into a PDF file fixer and we can view the flag
Flag: NEWBIE{Em0j!5_4r3_Coo!}
Category: Crypto
secsoc x csesoc
Potentially a substitution cipher, as the second and sixth segments could correspond to the “E” in “NEWBIE”. However jokes it’s just a binary ASCII encoding of the flag, whose dits are replaced with either csesoc or secsoc.
We can replace csesoc as 0 and secsoc as 1, then decode the segments.
Flag: NEWBIE{W3lC0m3_T0_th3_CtF}
Script: sol.py
Askii
Pretty simple challenge, each segment in the provided file is just the ASCII symbol.
The flag is embedded inside a chunk of lorem text, so just CTRL + F after decoding everything
Flag: NEWBIE{Ascii_Rul3s_Th0ugh}
Script: sol.py
Base64 Onion
The flag is encoded in base64 many times, just continually decode until we find the flag.
Flag: NEWBIE{N0_hop3_Ju5t_4dd1ng_l4y3rs}
Script: sol.py
Category: Recon
a rocket
An image of a US rocket is shown. A quick reverse image search as well as searching for “US Rocket” and checking its location reveals the location of Alabama
Flag: NEWBIE{Alabama}
Category: Misc
zippity 2: electric boogaloo
We need to SHA-512 a bunch of potential flags to find the flag whose hash begins with 146
The file turns out to be boogaloo-2042.txt.
Flag: NEWBIE{e#p4!8C_g%4-M!3&R_m%0$m#e?n@T!}
Script: sol.py
The Mining Canary
The flag is split into multiple payloads.
- HTML Comment:
NEWBIE{F12 - CSS Comment:
_Ctr1+sh1ft+I - Cookie:
_m0r3}
Flag: NEWBIE{F12_Ctr1+sh1ft+I_m0r3}
Plumbing Advice
question highkey stolen from skylight…
There’s a script tag in the source code that tries to source a script from a supposedly non-existent domain.
Check for TXT records with dig to find it (i.e. dig favicon.hakc.xyz TXT)
Flag: SKYLIGHT{dUg_f0r_trE4suRe_x_ic0n_m4rkEd_t#3_sp0t}

