Earlier today (18th January 2022), I was made aware of this rather humorous incident regarding a malicious actor submitted a false positive RAT result under our (New South Wales) health minister’s name. Whilst I don’t mean to sound asinine regarding the severity of COVID-19, or the severity of the crime committed (identity fraud, submission of false or misleading data) - I say humorous because from a software and cyber security perspective - there were massive oversights into the design of the reporting site; that if planned out properly would have mitigated this risk.
In humour, The “T” in NSW stands for “Threat Modelling”.
Or perhaps, the “R” in NSW stands for “Risk Assessment”.
That out of the way, let’s have a look at what went wrong, what went right, and how NSW could better prepare themselves for cases like these in the future.
The Issue - The Submission Process
Likely, malicious false positive results are being sent either out of spite (due to the lack of available RAT testing kits, government inability, or those other people) or someone wanting to make their rather mundane life abit more interesting by being a prankster - but what I care about is the technical aspect of this incident.
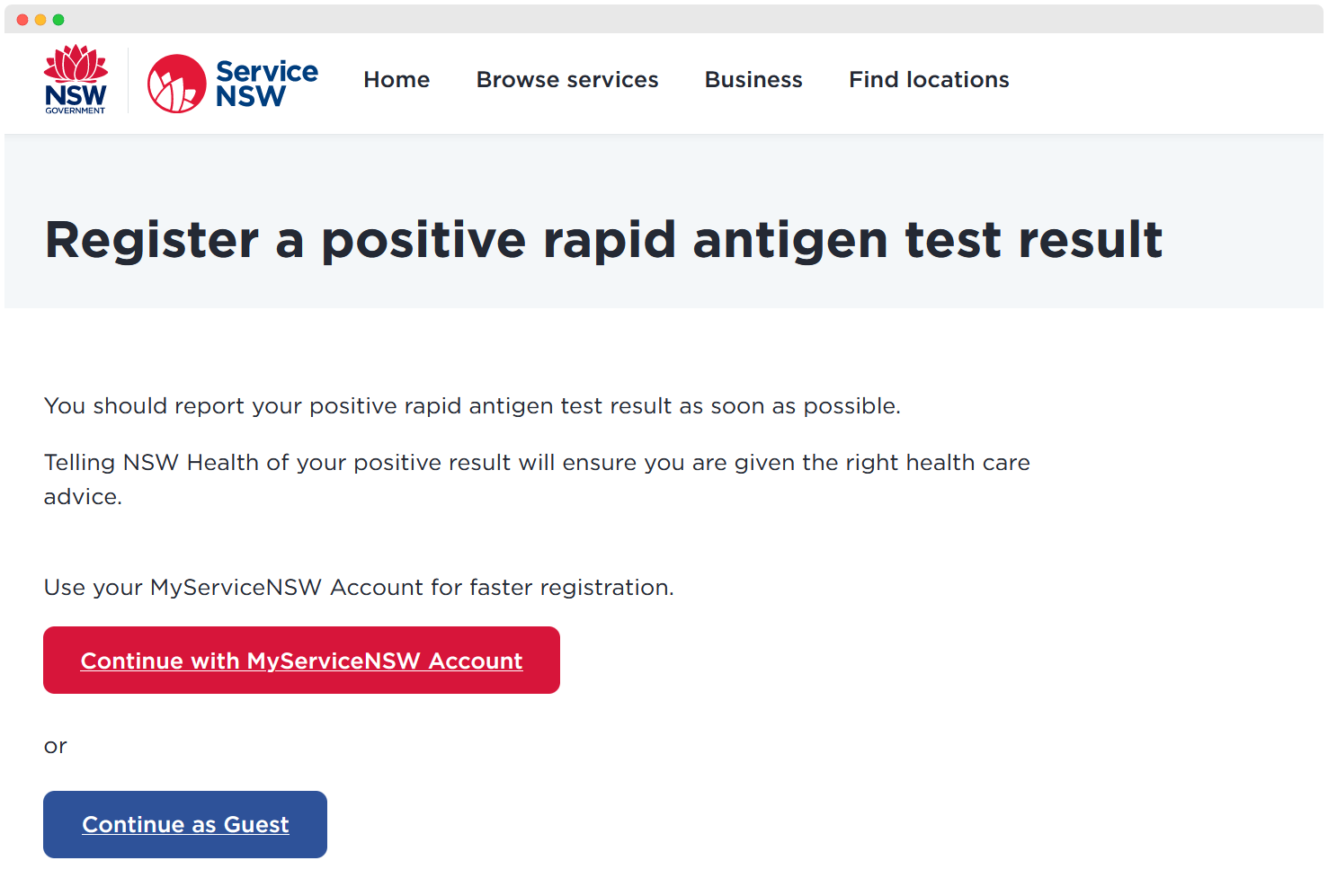
Taking a look at the submission website, we can see that we can proceed either as a logged in user, or as a guest.
- If continuing as a user
- Your submission will be logged against your user
- User sign-up requires providing PII (personally identifiable information)
- Other collected data: Submission time, IP address, browser user-agent, maybe some proprietary tracking data*?
- If continuing as a guest
- Your submission will be logged with the data you provide (all falsifiable)
- DOB, Name, Address, Contact Details
- Other collected data: Submission time, IP address, browser user-agent, maybe some proprietary tracking data*?
- Your submission will be logged with the data you provide (all falsifiable)
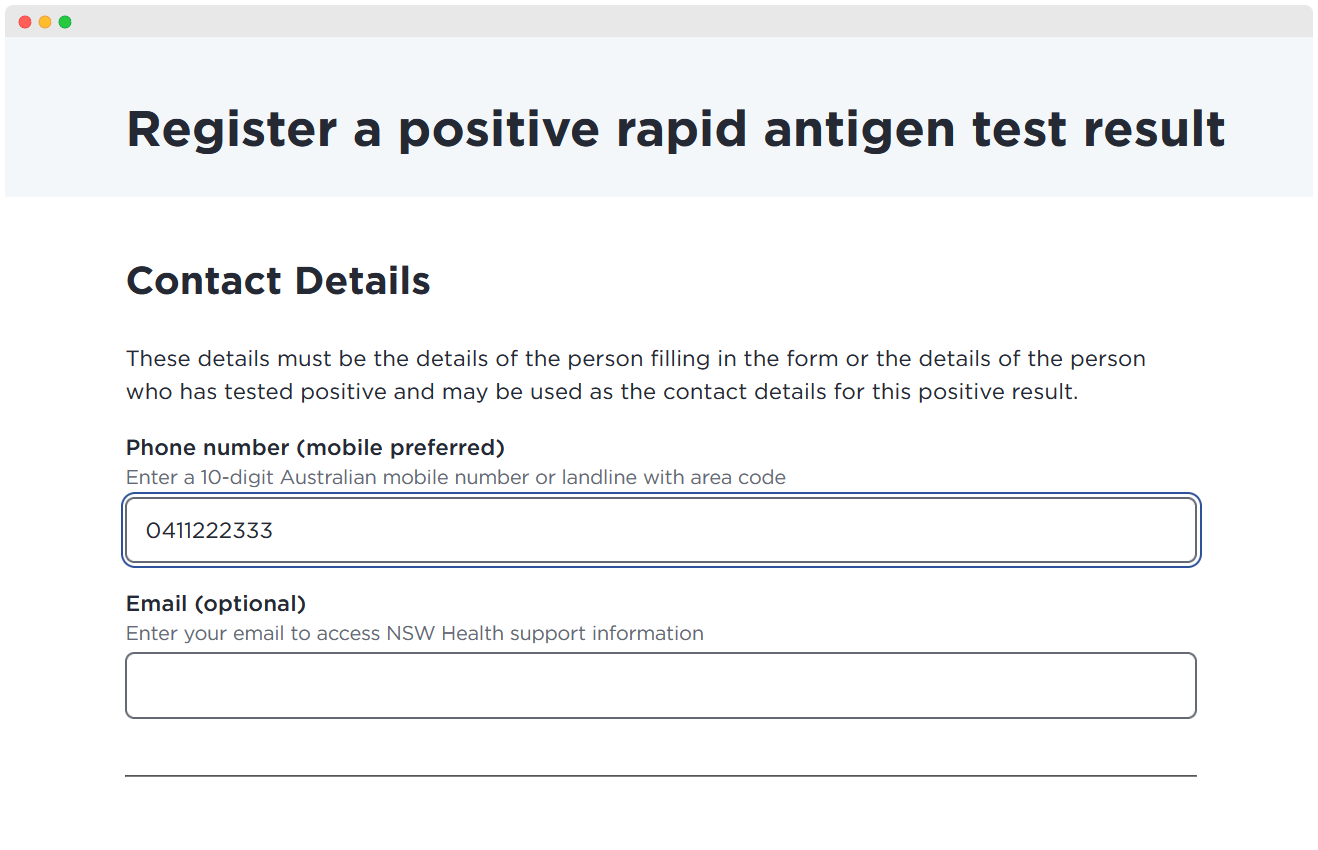
Looking at the submission form (N.B. of course, I won’t be actually submitting a report), the user can enter in any mobile number - true, fake, or false.
However as it seems to be, there is no Two Step Verification (2SV) of the mobile number. This means that anyone can enter in anyone’s number; and provided they’ve extensively anonymised* themselves from other identifiable data, it will be extremely difficult to find the culprit without any informant giving a tip.
Why would [2 Step Verification] prevent false reports?
It won’t. 😲
But what it will do is deter people from making false reports, else make legal investigations of these incidents easier.
As eponymously named, two step verification is a verification that requires two steps. You’ve all likely had to go through a 2SV process heaps of times (not to be confused with 2FA - Two Factor Authentication), needing to go to your email in order to sign up to some website. Likewise, 2SV on a mobile number means that in order to use a mobile number in a form (step 1), you need to prove that you have access to the number by providing a code / clicking a link that was sent to that number (step 2).
Welcome ${insert name here, or don’t}, so you’re a bad actor using a VPN with military grade encryption (whatever that means) secured by top men to hide your identity, and you need a valid mobile number to use which you have access to in order to submit this fake false positive RAT test result? Here are your options
Option One - I’ll use my own phone number
Well firstly that’s a dumb idea, it’s your own phone number. You might as well just hand yourself in to the police right now.Option Two - I’ll buy a new SIM card
In order to sign up to a mobile plan you need to provide some ID.Option Three - I’ll buy a new prepaid SIM card
Unless you activated a prepaid card before 2013, the Australian Telecommunications Act requires you to provide some ID in order to activate a prepaid mobile plan.Option Four - I’ll enter a random number and guess the verification code
Well.. I mean.. valid.. but…. uhh.. good luck?
Requiring 2SV on the phone number used during reporting would reduce the likelihood for people to submit fake reports; as they can no longer enter an arbitrary number without actually having access to that number. And on the off-chance that someone was ignorant to the fact that your mobile number can be used to identify you - the government would be able to figure out who owns the number that was used.
Now someone could of course steal someone else’s phone - you’d hope they would(n’t) just use a family member’s though…
Or perhaps use a fake ID - but that opens up a whole other can of worms.
What Should The Government Have Done / Do Next Time
Firstly, as I’ve already mentioned - implement 2SV of the mobile number; it acts as a deterrent but also as a tracing tool for the government.
But thinking ahead, the fact that 2SV was not implemented leads me to believe that NSW had rushed the design and development of reporting platform, overlooking any potential risks or threats that should have been obvious. The practice of threat modelling and risk management procedures are so important for any public / consumer / customer facing product; whether it be a physical product, a software product, an event, concert or what have you. It shocks me to have seen this happen on a government level. Must be intern szn or something…
Next time, plan things out carefully.
Slow and steady wins the race, not really.. but we’re pretty good at copying what other countries do anyway in response to COVID-19 - so why did we rush with this service?
That said, kudos to the designers and developers who were probably stressed out and pressed against time to
#pushtomaster
Software dev is hard, life is hard, sonder.
*Deanonymisation
By the way, despite what the Hollywood movie industry likes to portray, you cannot find someone’s exact location using their IP address - unless you’re a federal government agency (which you aren’t).
It’s just not how the internet works (in Australia at least…)
The issue with using VPNs or proxies to “hide” or “anonymise” your activity is that they are not fool-proof (See Computerphile’s explanation on how TOR works / doesn’t work) - whilst your activity may seem to be hidden, and now originating from some random jump host in America; at the end of the day your network activity will still pass through to, and be visible to your ISP, your first hop’s ISP, and your first hop’s server - not to mention any near-end, far-end and router nodes on the way. And whilst encrypting your data might prevent these parties from seeing the actual data being sent and received, they still know your activity. For example, who you are contacting to and for how long, etc. Match the submission timestamp with network activity happening at the same time and voila you’ve successfully been deanonymised.
In other words, the HTTPS and TLS buzz words really mean nothing - and we can’t fully trust VPN or proxy providers to not snitch on us!
Deanonymisation could also occur in other ways with tracking data (or the fact that these days websites are all interconnected together!).
Submitted a fake COVID-19 RAT report, but then use that very same device/account/computer/internet connection for some other government service?
Well gee thanks for telling us who you are!
The best way to avoid being caught for a crime, is to not commit the crime in the first place 🤔